
Encryption of data is a technique used to ensure data is kept confidential and read/write access to data/files and the information contained within them is only granted to the right users. This is especially important for businesses that manage a fleet of end user devices and are responsible for ensuring that they keep customer and private company information safe even if a single end device is lost or stolen. To do this organizations have to protect not only data in transit between networks and systems but also data at rest meaning the data stored on the physical devices themselves whether they are powered on or not.
Protecting data at rest in these circumstances, that is data leaks from a lost or stolen device, means preventing unauthorized access even when someone removes the hard disk/SSD/non volatile memory etc, gains access to the installed operating systems and or tries mount the associated storage drive from another operating system to read the contents. Providing protection necessitates having the right safeguards in place which is not only a matter of best practices but is essential because it means preventing leaks whether accidental or intentional that avoid reputational damage, regulatory fines which can be levied due to GDPR or similar rules, loss of competitive advantage, market price fluctuations in the shares that negatively impact investor confidence and shareholder returns due to leaked information that could cause a shift in public sentiment, and ultimately the protect the CEO, employees and or the executive leadership team from losing their jobs.
Therefore, to mitigate against these risks additional tooling to enure proper encryption is in place and managed across devices is required. While many consumer and business devices already come with some form of increasingly strong encryption baked into the hardware and or the Operating System (OS) this alone is not adequate without the supporting management functions. This is because in a corporate environment the software components managing this process are equally important because they provide simple mechanisms for generating the right keys and being able to remotely reset or unlock devices if the end users forget their credentials. For example, imagine a website where users had no option to reset their password but they had to create a complex and difficult to remember pass code in the first place and in the probably frequent event they forget are forced to use another service or to create a new account each time they forgot with no option to recover previous settings, transactions or data etc. This would be unacceptable, right? This is the exact situation that corporate IT would present to it's users if they didn't utilize encryption management tools.
Furthermore, being regulatory compliant for businesses comes with the added burden of requiring not just the ability to respond or the tools to prevent data breaches such as full end to end encryption both in transit and at rest but also the ability to prove this via audits and thorough reporting. That is the right management tools for device encryption need to be able to also report on the status of the entire device estate. To sum it all up, there is extra complexity in managing the process in a corporate settings where a plethora of users/devices exist. This problem is also not limited to big entities either as any group or company with over a few tens of devices to manage will quickly start to struggle to ensure proper data governance of which protecting data at rest is key with the basic consumer encryption management tools that do not cover managing and reporting on multiple devices.
To solve this challenge IT teams have traditionally employed tools from the likes of Symantec or Checkpoint to name a only few and these are quite good and up to the task. However, this article is not about those tools it is instead about an interesting encryption management suite available from Microsoft called MBAM (Microsoft BitLocker Administration and Monitoring) that few people are aware of which is available as a part of the Desktop Optimization Pack for no additional costs for customers who already have Microsoft Software Assurance.
MBAM leverages the BitLocker encryption capability that comes as a standard feature in recent releases of Windows since the Vista edition. Bitlocker provides full disk encryption ability on Windows and utilizes the hardware TPM chip included in most modern PCs to store the keys. An overview of the MBAM components and their roles is below:
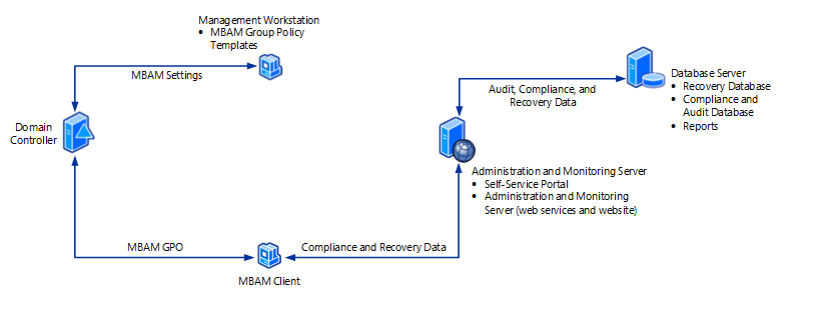
MBAM High Level Architecture
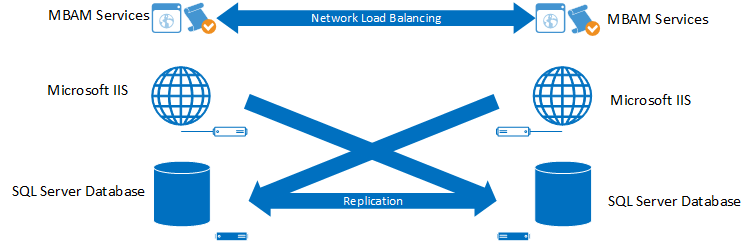
Redundant Services and Components for MBAM High Availability
MBAM Components
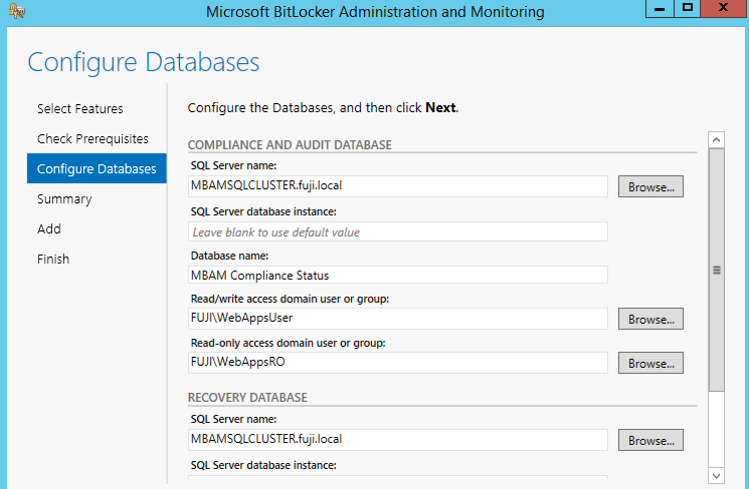
Compliance and Audit Database
These features are configured on a server running Windows Server and a supported version of an SQL Server instance.
The Compliance and Audit Database
The Compliance and Audit Database stores compliance data, which is used primarily for reports that SQL Server Reporting Services hosts.
Recovery Database
The Recovery Database stores recovery data that is collected from MBAM client computers and can be hosted on the same host as the Compliance and Audit Database.
Reports
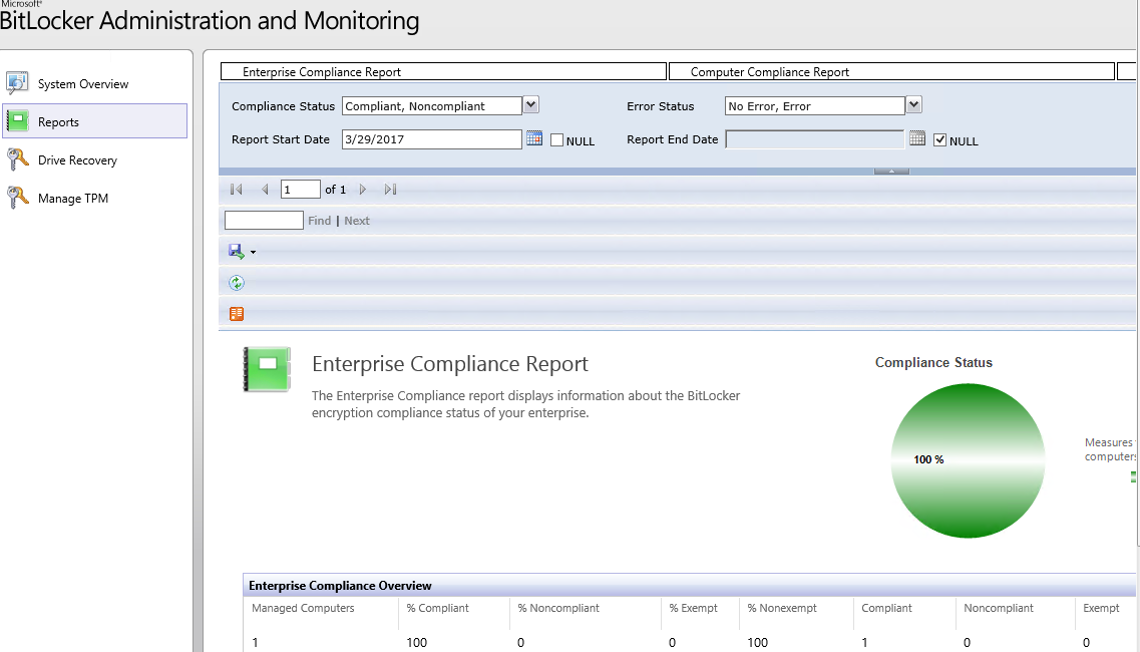
Reports provide recovery audit and compliance status data about the client computers in your enterprise. You can access the reports from the Administration and Monitoring Website or directly from SQL Server Reporting Services.
Administration and Monitoring Server
The Administration and Monitoring Website is used to:
-
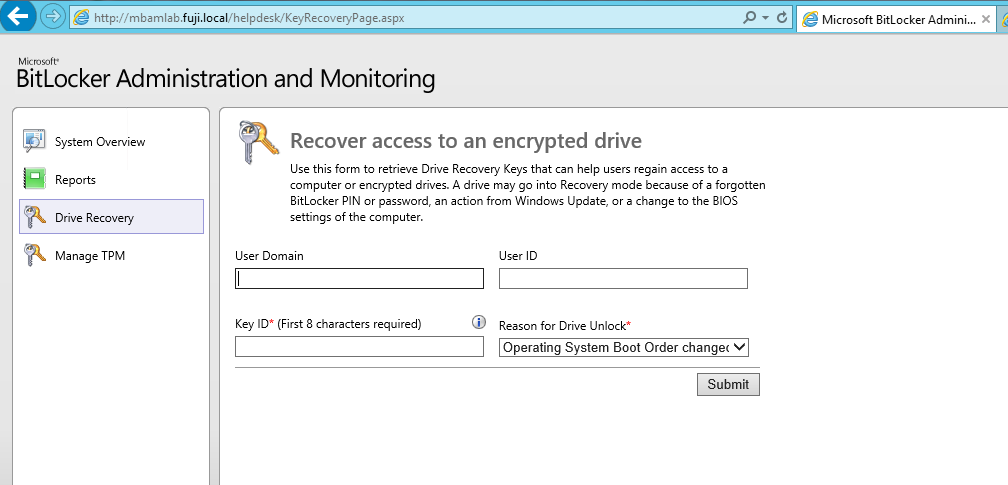
Help end users regain access to their computers when they are locked out. (This area of the Website is commonly called the Help Desk.)
-
View reports that show compliance status and recovery activity for client computers.
Self-Service Portal
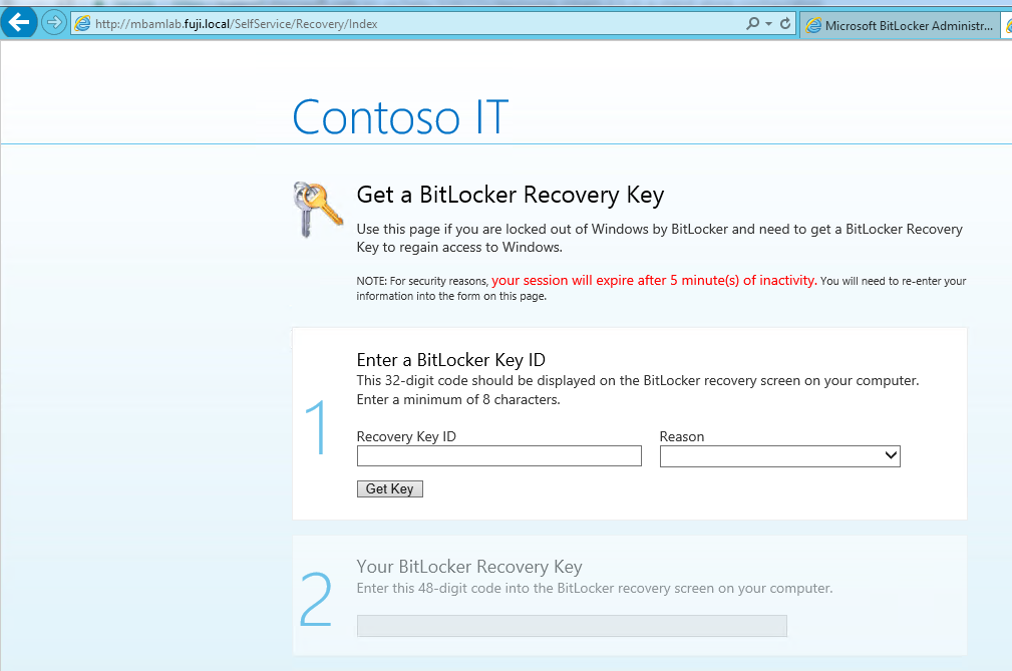
This feature is configured on a computer running Windows Server with the IIS roles. The Self-Service Portal is a website that enables end users on client computers to independently login to a website portal to get a recovery key if they lose or forget their BitLocker password.
Monitoring Web Services
The monitoring web services are backend processes/service daemons used by the MBAM Clients as well as the website portals to communicate to the MBAM database.
Deploying MBAM
In the next section we detail using screenshots a few of the steps required to deploy in MBAM in your environment in HA configuration using the architecture above. A more indepth tutorial can be found on Microsoft documentation site for MBAM, reading this guide, or by watching this video or this video.
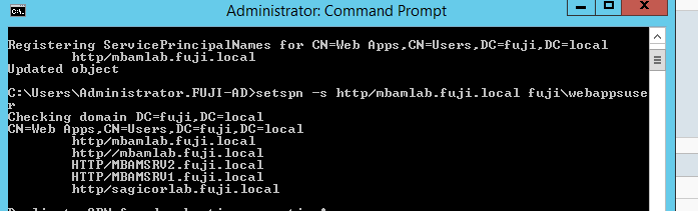
Step 1 - Register SPN for the application Pool Account on the Domain Controller
This is how the client is able to authenticate to the web services using Kerberos.
Step 2 - Configuring SQL Database/s
We are using multiple databases here for redundancy which is recommended but not necessary for a production setup.
SQL Failover Cluster
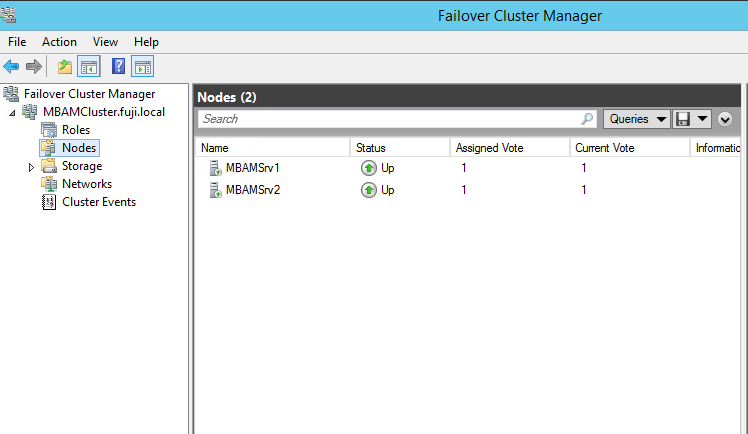
SQL High Availability Group
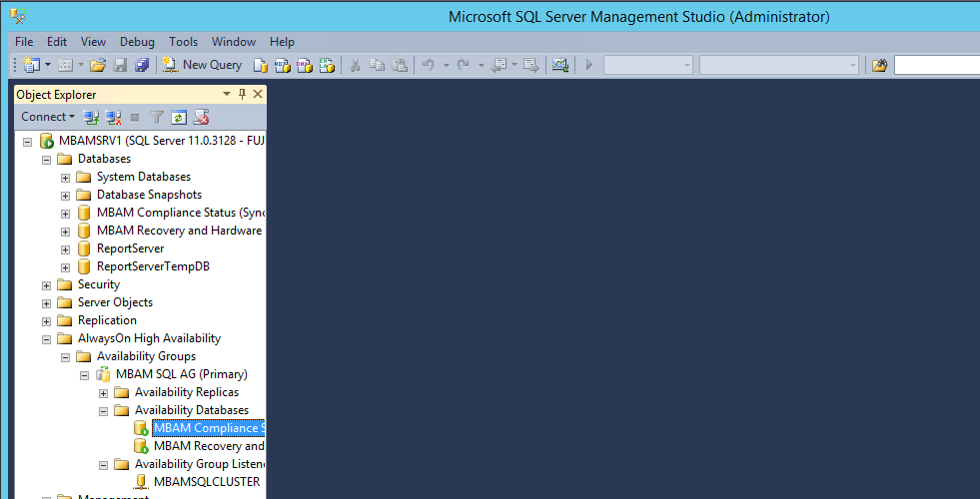
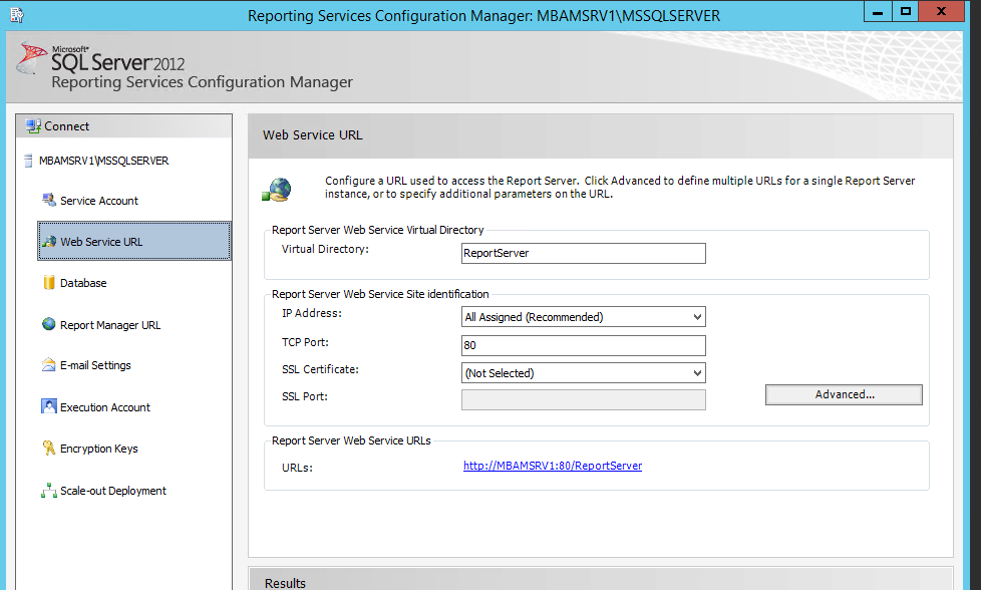
SQL Reporting Services
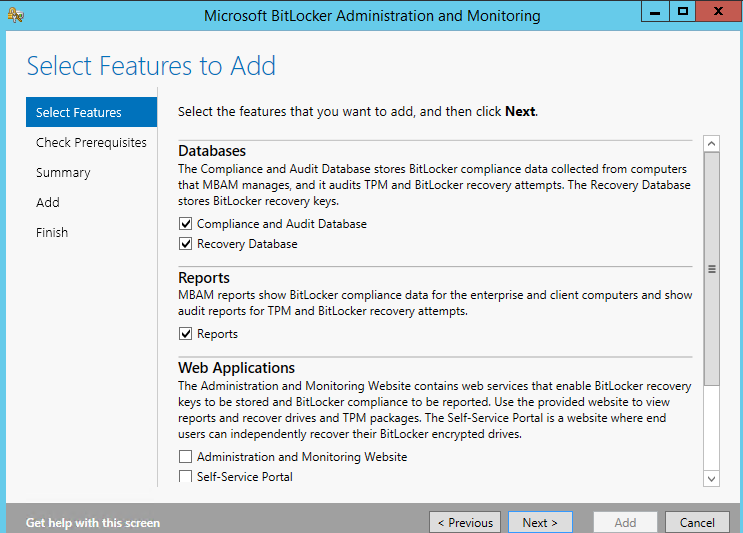
Step 3 - Install the MBAM Components from the installer
MBAM Compliance and Auditing Feature and Configure
Administration and Monitoring Website and Self-Service Portal
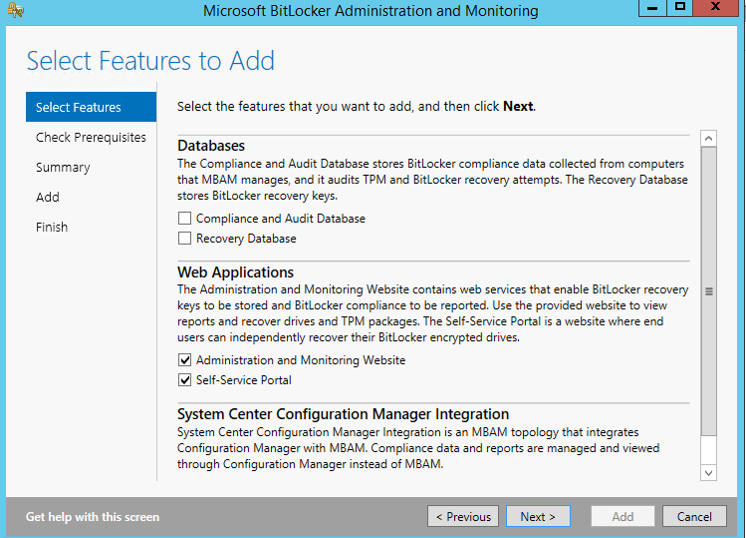
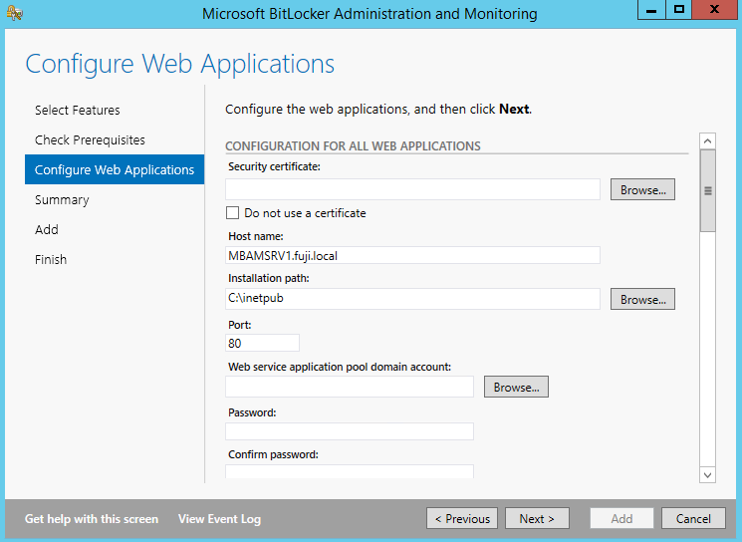
Step 4 - Configure Network Load Balancing (NLB) for the IIS service
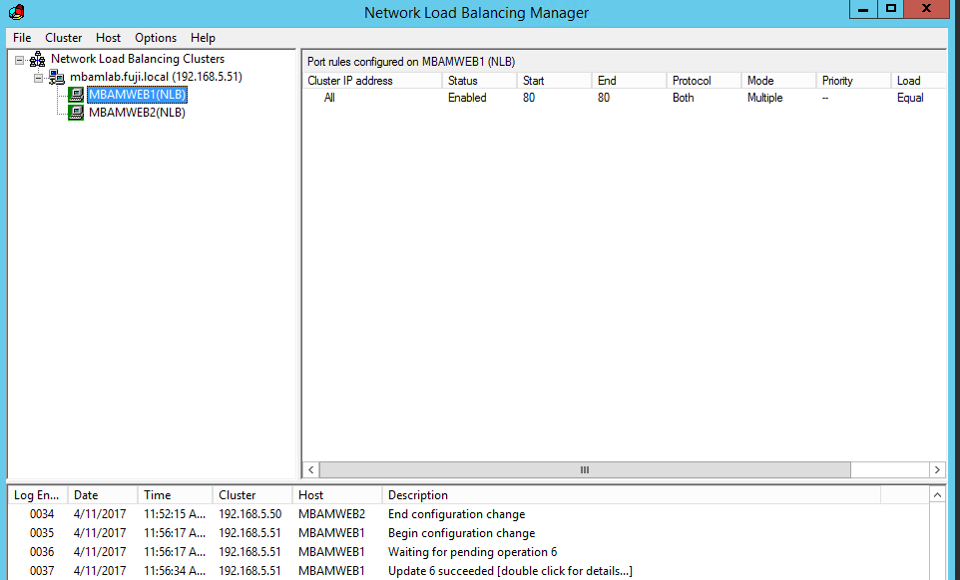
Step 5 - Validation and Testing
Administration using the Administration and Monitoring Website
Viewing Reports
Drive Data Recovery
Self-Service for End Users
Data Recovery from Self-Service Portal
 Nneko Branche.
Nneko Branche.